Murphy’s F-ing Law.
In my past few T_IM articles I’ve went on and on about security for your WordPress websites, and what to do to protect your website from hackers.
So of course – I was hacked.
This wasn’t a case of not practicing what I preach thankfully – instead it was a case of I just didn’t quite do enough.
In this article I’m going to talk about the hack, what happened, the traffic and search engine effects, and what I’ve did to HOPEFULLY counter this in the future, as well as what to do in a situation like this.
Let’s get to it:
My Initial Precautions:
First of all, let’s cover what I have done security wise on my websites BEFORE this hack occurred:
- WordPress & All Plugins updated monthly.
- Unique username for any admin logins.
- Login lockdown plugin installed to block any brute force attacks.
- Firewall running on server.
Those are the basics. There are a few other things I do, as well as nightly/weekly/monthly backups of everything as well. Keeping track of all possibly security warnings and fixing them(sslv3 POODLE for example). But it wasn’t enough.
What Exactly Happened?
On December 8th, my partner on the site OrderOfBooks.com messaged me to let me know that his web browser, Firefox, was saying OOB was an attack page.
I immediately logged on and checked and had the same message in Chrome.
I viewed the source code and found some iframe code thrown in at the bottom of the site that was embedding a URL. On further exploration I found a widespread hacking job throughout the website.
The Most Important Thing: Don’t Panic
When something like that happens – the most important thing you can do is not to panic.
Immediately contact your web hosts – call them up if you can. Get them on this and figure out exactly how your website was infiltrated to stop this in the future, and plug any future holes.
The most important thing by far is to find out how they got in, and stop that from happening in the future. Not just for this website – but for all websites that you own.
Unfortunately – I Panicked
It happens. It came at a bad time. I was done work for the day, and busy in the kitchen preparing a lengthy meal. I had plans that night and couldn’t drop everything for this.
On top of that – December is a crucial month for that website. It’s when we do DOUBLE our average income. So my mindset was basically “I need to fix this ASAP”.
I cleared up the error, found malicious files and removed them, changed login details, as well as ran scans on all WordPress, WordPress Plugins and WordPress theme files(more on that later) to check if any had been modified from the originals. Some had, and I fixed all of them.
Unfortunately all of this meant that my hosts couldn’t determine how the hacker actually got in. It looks like they were able to access the WordPress backend via a server side brute force script that they had uploaded – but we weren’t able to determine how they were actually able to upload that.
Either way – yeah; don’t panic like I did! Take a deep breath then contact your hosting company. They have a whole department that is experienced with this sort of thing.
Once The Malware Is Removed:
Once removed, you need to contact Google and get removed off the blacklist.
This steps generally quite easy – you’ll log into Webmaster Tools and there’ll be a message there notifying you that they have found Malware on your website. You can then check the box and basically tell them it’s removed(as well as maybe tell them what happened, and what steps you’ve taken) and they’ll take a look at it and if all removed, they’ll remove your site from the blacklist.
Quick note on this process: they’ll remove it within 24 hours, usually less. If you’ve hit the 24 hour mark and still nothing, then resubmit the request. It’s possible it got you lost in the shuffle, and it won’t move you back in a queue or anything like that.
What Where The Search/Social Effects Of This?
The issues were with the following: Google, Twitter, Mozilla Firefox, Google Chrome.
All 4 quite rightly, flagged the website. Chrome and Firefox would make it so you couldn’t visit the site, while Google also had a warning in their search results. Twitter blocked all postings of the URL.
Some screenshots showing all this….
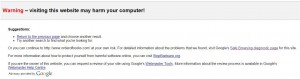
Google listing warning people this site may harm their computer:
If you click that “site may harm computer” link it takes the person to a page notifying them that the website may install malicious software on their computer.
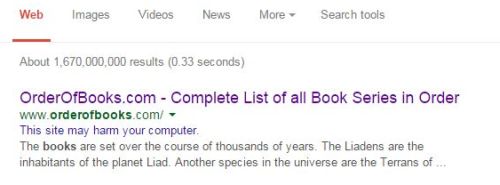
This screenshot – click for big – if you try and visit the website by clicking on that link via Google:
As you can see, absolutely no way to say “Yeah whatever”, and click. The user has to actually type our address in the address bar instead – and really with that sort of warning why would they do that?
And if they DO attempt to go via the address bar anyway?
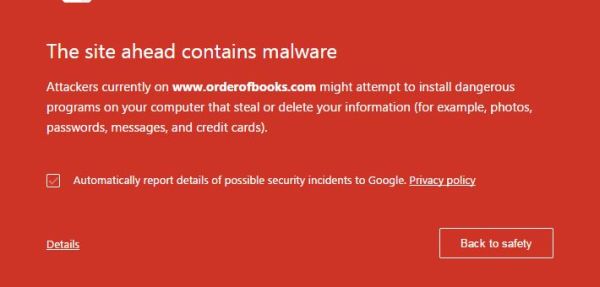
That’s the warning if they use Chrome. Firefox offers a similar message.
Now you can click to read the details there, and in that section they tell you Google detected malware but you can visit anyway. But again really – after all those steps, how many people do you think are going to click? Our traffic numbers showing we got just 2.6% of the Firefox and Chrome users we’d normally get pretty much tells the full story there.
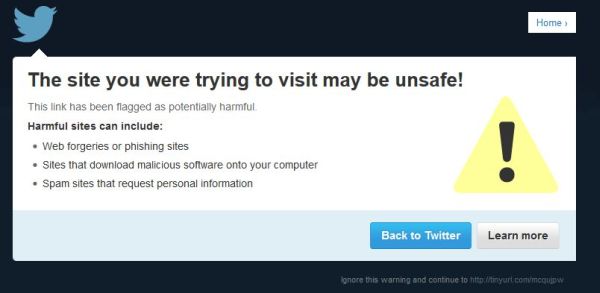
Quick Note about Twitter: Unfortunately, 2 weeks after the fact, Twitter still has the website flagged and has not removed it from their malware list despite multiple requests sent to them. I did attempt to circumvent it by using a URL shortener. That’d allow the URL to be posted – but they have their own internal malware system. Anyone clicks on the link and this pops up:
What Were The Traffic Effects?
Not as bad as you’d think.
Here’s a screenshot from Analytics showing the unique visitors over that period:
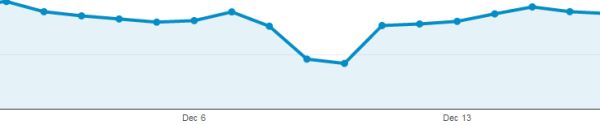
We lost around 50% of our traffic during the downtime. That’s a LOT of users and financial losses in the $x,xxx range but really – it could have been a hell of a lot worse.
I mean look at all the issues above with Chrome and so on. Thankfully there were enough people using IE, Safari, Amazon Silk and other browsers who would also search via Bing and other search engines that it didn’t hurt as much as it could have.
Also dealing with it promptly obviously helped – we were able to regain our usual traffic IMMEDIATELY. There were no ranking losses or any of that kind so yeah; that was very nice.
Future Precautions:
The first thing I realized was that having a unique username and strong password for WordPress just wasn’t enough. First of all – WordPress is a bitch with putting your username up all over the site or in urls etc even if you try and get it not to.
And as there is not a big userbase logging in via WordPress to that or 98% of my sites, I realized I could do an IP block. This is what I have on my .htaccess now for my sites:
order deny,allow
Deny from all
# whitelist Dealer Dan
allow from XXX.XXX.XXX.XXX
The XXX’s are my IP Address. Essentially that blocks any other IP address from being able to log in to WordPress.
Wordpress plugin security wise – they are two options: Sucuri and Wordfence.
Personally – I went with Wordfence. I tried them both out, I spent a couple of hours going through them all and reading the net etc – and ultimately I decided on Wordfence. Hard to say why other than I just like it better. Security wise they’re probably both similar – I just preferred the interface better.
Based on a default install, here’s the steps I take upon installation:
- Give it my e-mail address so it can e-mail me any alerts.
- Enable auto-update.
- Live-Traffic: Turn that off.
- Head to the “Options”
- Update the Alerts. Uncheck “Alert me when someone with administrator access signs in
- Under “Scans to Include” I select ALL of the options except High Sensitivity Scanning. Only time you want that on is if you were hacked.
- Under Login Security options – as I have wp-login blocked I don’t bother with this, but you may want to set stuff like lock out after 3 login failures, and 3 forgot password attempts, as well as change the login time to much longer.
- Add my IP Address under “Other Options” to the whitelist block.
- Change “Maximum execution time for each scan stage” to 15 seconds.
- Run a scan.
- Fix any issues.
- Drink a sarsparilla.
I don’t touch anything else. I use WP Super Cache for example so I don’t need any of the cache options.
Also any issues – be sure to look into them before immediately telling Wordfence to restore a core file or whatever. Find out what it is – it could be legitimate. It could be a false positive, or it could be your coder edits core files or something stupid like that. Either way just don’t blindly be like “Yep do that”. The whole thing is REALLY sick though. It will show you exactly what was modified. Here was an old readme file that hadn’t been updated from a plugin:
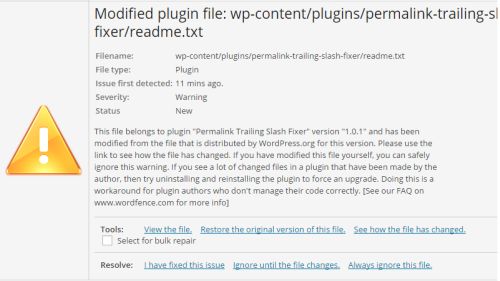
And what happens when you click “See how the file has changed”:
From doing research, some people immediately block fake google crawlers. I don’t bother with that because I don’t think it’s necessary; and it stops any chance of it accidentally blocking something legitimate.
I also don’t choose to participate in the Wordfence security network. I uncheck that. That’s just a personal issue.
However with anything like this – take some time to learn about the settings. You may want stricter firewall rules etc – it’s totally up to you. Each option has a little information button beside it and you click that, and it breaks it down for you.
I should note I’ve ran speed tests when it is scanning etc and found absolutely zero issues with slowdown so that’s nice.
Oh and finally – on the options page you can actually choose to export your settings. If you run over 50 freaking websites like me – you’ll find that rather useful!
Whew – okay that is everything.
Now I just have to sit back and wait for my websites to get hacked despite all this.
Murphy’s f-ing law.

 Dealer Dan, pictured here with WWE Superstar Mick Foley, has been in internet marketing since 1996. He likes hugs, long walks on the beach, and making money while wearing his jammy jams. For more information, you can read all
Dealer Dan, pictured here with WWE Superstar Mick Foley, has been in internet marketing since 1996. He likes hugs, long walks on the beach, and making money while wearing his jammy jams. For more information, you can read all